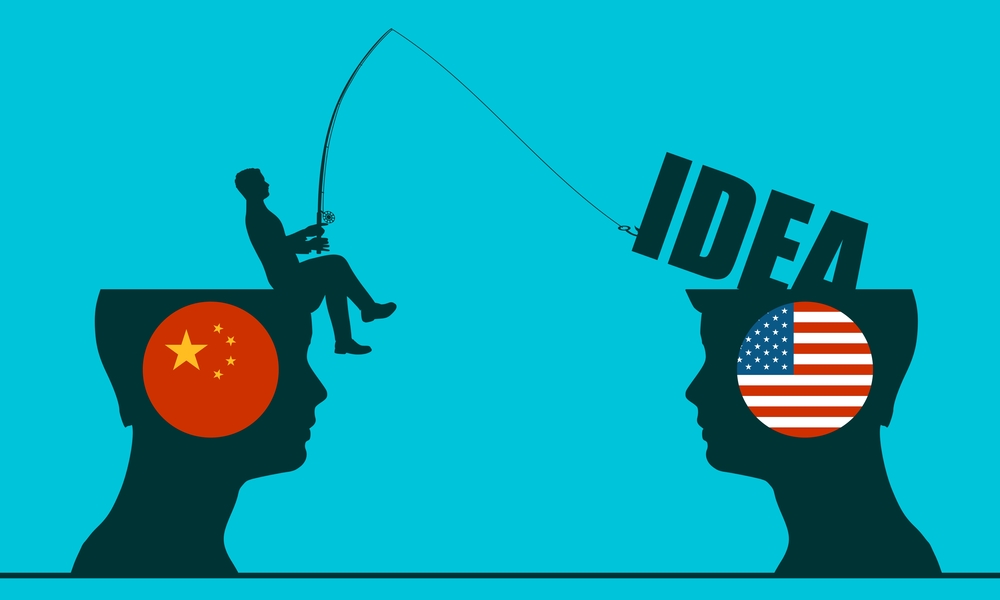
As China continues to steal American technology, here we show the ways in which the Communist government rips off the US, including a timeline of recent events.
When the Pentagon appointed its first director for protecting critical technology, he was given one simple instruction to stop China from exfiltrating US tech, “Be bold, break glass, don’t accept the status quo.”
‘China Has Database on Vulnerabilities of Millions of Americans’ https://t.co/Exoim4xiyp
— Information Warfare Community Self Synchronization (@IWCsync) November 12, 2019
It is not usual for the Pentagon to operate in such a way that is reminiscent of Facebook’s old slogan, “move fast and break things.”
But when it comes to American technology being siphoned off to China, the Pentagon is taking the gloves off.
“We tend to be more measured, but I have a time-limited task force. I don’t have time to go slow and steady. And neither does our nation when it comes to losing our critical technology to China,” said Maj. Gen. Thomas E. Murphy, director of the Protecting Critical Technology Task Force, in a statement.
“We need everyone in this business to smarten up”
According to the intelligence community, the US is losing critical technology to China in several ways through both legal and illegal means:
- Straight-up Hacking: Chinese government hackers have engaged in a prolonged campaign in recent years to build a massive database on American citizens for intelligence and counter-intelligence purposes.
- By exfiltrating data from the US Government (USG) Office of Personnel Management (OPM), health insurers (e.g. Anthem), airlines (e.g. United) and hotel chains (e.g. Marriott), among others, China’s intelligence services have access to an incredibly rich database on the behavior, preferences, and vulnerabilities of hundreds of millions of Americans.
- Acquiring Foreign Companies and Harvesting Their Data: When a Chinese company buys an American company, it gets all the technology the American company owns, including defense capabilities.
- Any Company Operating in China Must Surrender its Data: By law any company operating in China will have to hand over its data to the Communist government. The Chinese government will have lawful and technical access to all digital data within its borders and perhaps to large volumes of data beyond its borders.
- Infiltrating Universities and Research Centers: China has over 200 recruitment programs in which the Chinese government offers lucrative financial and research benefits to recruit individuals working and studying outside of China who possess access to, or expertise in, high-priority research fields.
- All programs are overseen by the Chinese government and are designed to support its goals, sometimes at US taxpayers’ expense, according to the FBI.
Timeline: US, China Relations News From November
November was a tumultuous month for US/China relations, especially with regards to tech. Here is a brief timeline of events that occurred last month:
- November 5: A hearing in the Senate revealed that China is creating databases on the behavior, preferences, and vulnerabilities of hundreds of millions of Americans to use for intelligence purposes.
- November 5: Senator Josh Hawley warns that TikTok may be controlled from Beijing, and the data could be used to train China’s AI systems.
- November 15: FBI Director says, “China is the single greatest counterintelligence threat we face,” especially on the economic espionage side.
- November 18: Senator Hawley introduces the “National Security and Personal Data Protection Act” to “combat the flow of Americans’ sensitive personal data to hostile foreign countries – including China and Russia – that pose a threat to America’s national security.”
- November 18: CNN reports, “Beijing tells US to stop ‘flexing muscles’ in South China Sea.”
- November 19: FBI declares, “Beijing aims to acquire our [American] technology—often in the early stages of development—as well as our expertise, to erode our competitive advantage and supplant the United States as a global superpower.”
- November 19: Nature reports, “Chinese infiltration of US labs caught science agencies off guard: new details of China’s efforts to infiltrate US research institutions.”
- November 24: International Consortium of Investigative Journalists reports that China is using predictive policing by algorithm to detain thousands of Uighurs in reeducation camps. “Chinese police are guided by a massive data collection and analysis system that uses artificial intelligence to select entire categories of Xinjiang residents for detention.”
- November 26: Chinese video sharing app TikTok suspends account of a 17-year old American who criticized China’s “concentration camps” and other humanitarian abuses.
- November 27: Hong Kong Human Rights and Democracy Act of 2019 is signed into law.
- November 28: Gobble, Gobble.
NEW: While a TikTok exec was on-air at CNBC refuting allegations of censorship, the Washington Post ran a story about a user in the U.S. who was locked out of her account after her post criticizing China went viral.https://t.co/skhF0RcYo2
— Will Feuer (@WillFOIA) November 26, 2019
Now as we enter December we are already seeing that China is expanding its use of facial recognition software with “regulations that require Chinese telecom carriers to scan the faces of users registering new mobile phone services,” according to Reuters.
China’s Communist regime has a horrendous history of human rights abuses, and today we are seeing these abuses continue from Hong Kong to Xinjiang.
The abuses, while human in origin and nature, are all powered by technology — a lot of which was stolen from the US and used for nefarious purposes.
This includes the cover ups of abuse through censorship, which is also spreading to the US as evidenced by the actions of TikTok.
General Murphy said that “We are in a fight every day with our strategic competitors on our university campuses, in our businesses, in cyberspace. And the prize is military technological advantage.
“We need everyone in this business to smarten up and to have a shared belief of the threat, and a sense of urgency to correct the path that we are currently on.”
China’s data theft and the supreme art of subduing without fighting